Sniper - Hack The Box

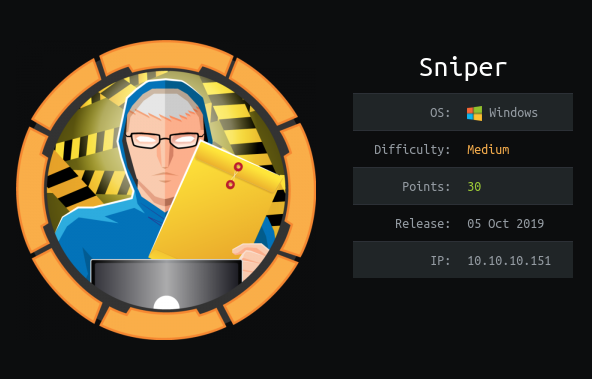 Sniper is a Medium Windows machine. Initial foothold involves exploiting the LFI at /blog endpoint . we create a username with powershell encoded input at /user endpoint and execute them using LFI to ge a revershell as iusr. Next we uploaded nc to chris user home and triggered it to get a revershell as that user. Privilege escalation involves generating malicious chm file using Nishang and we get reverse shell as Administrator.
Sniper is a Medium Windows machine. Initial foothold involves exploiting the LFI at /blog endpoint . we create a username with powershell encoded input at /user endpoint and execute them using LFI to ge a revershell as iusr. Next we uploaded nc to chris user home and triggered it to get a revershell as that user. Privilege escalation involves generating malicious chm file using Nishang and we get reverse shell as Administrator.
 Forest in an easy difficulty Windows Domain Controller (DC), for a domain in which Exchange Server has been installed. The DC is found to allow anonymous LDAP binds, which is used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold. The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes.
Forest in an easy difficulty Windows Domain Controller (DC), for a domain in which Exchange Server has been installed. The DC is found to allow anonymous LDAP binds, which is used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold. The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes.
 Postman is an easy difficult Linux machine, which features a Redis server running without authentication. This service can be leveraged to write a SSH public key to the User’s folder. An encrypted SSH private key is found, which can be cracked to gain user access. The user is found to have a login for an older version of webmin. This is exploited through command injection to gain root privileges.
Postman is an easy difficult Linux machine, which features a Redis server running without authentication. This service can be leveraged to write a SSH public key to the User’s folder. An encrypted SSH private key is found, which can be cracked to gain user access. The user is found to have a login for an older version of webmin. This is exploited through command injection to gain root privileges.