Cascade - Hack The Box

 Cascade is a medium difficulty windows machine. which resembles a real-life Active Directory Attack Scenario. Initial foothold involves in getting base64 encode password of r.thompson user from ldap enumeration. With help of those credential we get VNC_Install.reg registry file from Datas.smith share on the box. I contains hex encrypted string we crack it to get s.smith creds and login as s.smith user. Next, we’ll get ArkSvc user encrypted password from Audit.db from Audit$ share and we also grab all the exe and dll file from that share. which helps us to crack the encrypted string. Once we got the ArkSvc user we login to the machine and see his a part of AD Recyle Bin group and we can retrive AD deleted objects and their properties. We managed to retrive TempAdmin base64 encrypted password and we decrypt and use the same password to login as Administrator.
Cascade is a medium difficulty windows machine. which resembles a real-life Active Directory Attack Scenario. Initial foothold involves in getting base64 encode password of r.thompson user from ldap enumeration. With help of those credential we get VNC_Install.reg registry file from Datas.smith share on the box. I contains hex encrypted string we crack it to get s.smith creds and login as s.smith user. Next, we’ll get ArkSvc user encrypted password from Audit.db from Audit$ share and we also grab all the exe and dll file from that share. which helps us to crack the encrypted string. Once we got the ArkSvc user we login to the machine and see his a part of AD Recyle Bin group and we can retrive AD deleted objects and their properties. We managed to retrive TempAdmin base64 encrypted password and we decrypt and use the same password to login as Administrator.
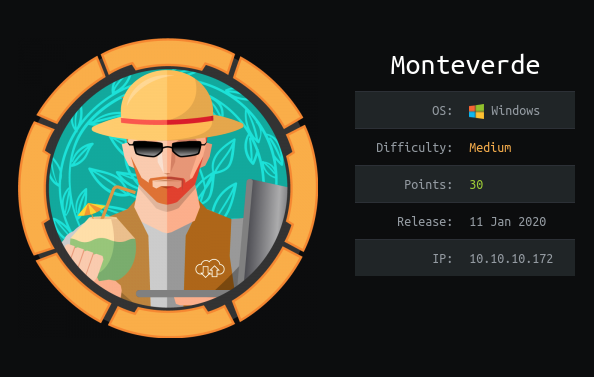 Monteverde is and medium difficult Windows machine, It’s Active Direcoty box. Initial foothold involves guessing the weak passwords for the users. Later, password for mhope user is discloded through azure.xml file which left unattended in users$/mhope share. We find that mhope user is member of azure admins group. we Abuse Azure AD Connect Service to extract the credentials of Administrator.
Monteverde is and medium difficult Windows machine, It’s Active Direcoty box. Initial foothold involves guessing the weak passwords for the users. Later, password for mhope user is discloded through azure.xml file which left unattended in users$/mhope share. We find that mhope user is member of azure admins group. we Abuse Azure AD Connect Service to extract the credentials of Administrator.
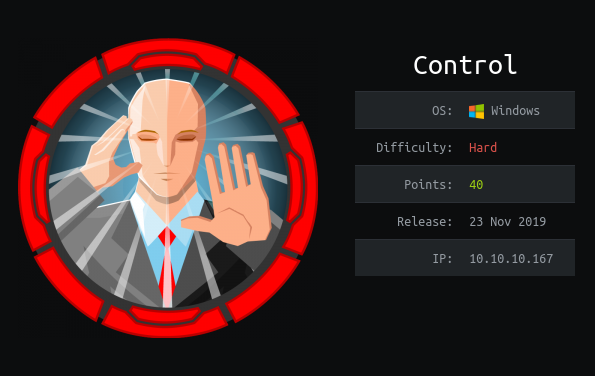 Control is hard difficulty Windows machine featuring a Corporate Interal website which we can access through proxy and it is vulnerable to SQL Injection. This leverage to extral MySQL usersname and password hashes, and also write webshell using SQLi to gain the Initial foothold. By cracking the password hash of hector user helps us to move laterally to his windodws account. Examining the Powershell history file reveals that Registry Permissions may have been modified. After Enumerating Registry Service permissions and other service properties, seclogon service is abused to escalate shell as NT AUTHORITY SYSTEM.
Control is hard difficulty Windows machine featuring a Corporate Interal website which we can access through proxy and it is vulnerable to SQL Injection. This leverage to extral MySQL usersname and password hashes, and also write webshell using SQLi to gain the Initial foothold. By cracking the password hash of hector user helps us to move laterally to his windodws account. Examining the Powershell history file reveals that Registry Permissions may have been modified. After Enumerating Registry Service permissions and other service properties, seclogon service is abused to escalate shell as NT AUTHORITY SYSTEM.
 Bounty is an easy difficulty Windows machine, which features an interesting techniques to bypass file uploader protections and achieve code execution. Privileges escalation invloves abusing SeImpersonatePrivilege. This machine is also vulnerable to multiple privilege escalation vulnerabilites. Which highlights the importance of keeping system upto date with latest security patches.
Bounty is an easy difficulty Windows machine, which features an interesting techniques to bypass file uploader protections and achieve code execution. Privileges escalation invloves abusing SeImpersonatePrivilege. This machine is also vulnerable to multiple privilege escalation vulnerabilites. Which highlights the importance of keeping system upto date with latest security patches.
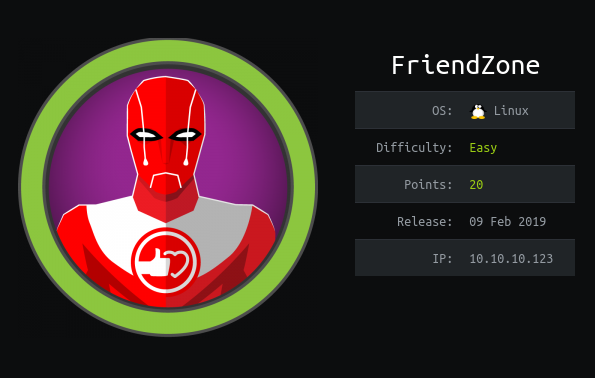 Friendzone is an easy difficuly Linux machine. which needs fair amount of enumerations. Intial foothold invovles doing a DNS zone transfer and discover vhosts. Open shares are available through smb which provides credential for admin page. LFI in dashboard.php is leveraged to get RCE. A cron job is running using writable module, making it vulnerable to hijacking.
Friendzone is an easy difficuly Linux machine. which needs fair amount of enumerations. Intial foothold invovles doing a DNS zone transfer and discover vhosts. Open shares are available through smb which provides credential for admin page. LFI in dashboard.php is leveraged to get RCE. A cron job is running using writable module, making it vulnerable to hijacking.
 Conceal is a hard difficulty windows machine which teaches enumeration of IKE protocol and configuration of IPSec in transprt mode. Once configured and we can bypass the firewall and shell can be uploaded via FTP and executed. On listing the hotfxes the box is found vulnerable to ALPC TASK Scheduler LPE. Alternatively, SeImpersonatePrivilege granted to the user allows to obtain a SYSTEM shell.
Conceal is a hard difficulty windows machine which teaches enumeration of IKE protocol and configuration of IPSec in transprt mode. Once configured and we can bypass the firewall and shell can be uploaded via FTP and executed. On listing the hotfxes the box is found vulnerable to ALPC TASK Scheduler LPE. Alternatively, SeImpersonatePrivilege granted to the user allows to obtain a SYSTEM shell.
 Swagshop is a easy difficulty linux machine which running old version on Magento. It is vulnerable to SQLi and RCE which leads to shell as www-data. Privilege escalation invovles the www-data can use vim in the context of root which is abused to execute commands as root.
Swagshop is a easy difficulty linux machine which running old version on Magento. It is vulnerable to SQLi and RCE which leads to shell as www-data. Privilege escalation invovles the www-data can use vim in the context of root which is abused to execute commands as root.
 Chatterbox is a Easy difficulty windows machine. Intial foothold involves exploit a Buffer overflow on AChat applications. later we abuse file permission using icacls to read the files inside Administrator directory. Auto Login is enabled for Alfred user. So, we can Obtain Auto login credential Using PowerUp. Next, by using the same password for Administrator works and we can login as Administrator.
Chatterbox is a Easy difficulty windows machine. Intial foothold involves exploit a Buffer overflow on AChat applications. later we abuse file permission using icacls to read the files inside Administrator directory. Auto Login is enabled for Alfred user. So, we can Obtain Auto login credential Using PowerUp. Next, by using the same password for Administrator works and we can login as Administrator.
 Registry is a hard difficulty linux machine, which features Docker and Bolt CMS running on Nginx. Docker registry API access is configured with default credentials, which allows us to pull the repository file. We gain intital foothold using the private key present in those repositories. User credentials for Bolt CMS can be obtained, and exploiting the CMS provides us with access to the www-data user, who has sudo entry to perform backups as root using the restic program. After taking a backup of the root folder remotely and mounting the repository with restic, with help of root priveate key we ssh as root.
Registry is a hard difficulty linux machine, which features Docker and Bolt CMS running on Nginx. Docker registry API access is configured with default credentials, which allows us to pull the repository file. We gain intital foothold using the private key present in those repositories. User credentials for Bolt CMS can be obtained, and exploiting the CMS provides us with access to the www-data user, who has sudo entry to perform backups as root using the restic program. After taking a backup of the root folder remotely and mounting the repository with restic, with help of root priveate key we ssh as root.
 Jarvis is a medium difficulty Linux box running a webserver, whicha has DoS and brute force protection enabled. A page is found to be vulnerable to SQL Injection, Which requires manual exploitation. This serivce allows the writing of a shell to the web root for the foothold. The www-data user is allowed to execute script as pepper user, and the script is vulnerable to command Injection. On further enumeration, systemctl is found to have SUID bit set, which is leveraged to gain a shell as root.
Jarvis is a medium difficulty Linux box running a webserver, whicha has DoS and brute force protection enabled. A page is found to be vulnerable to SQL Injection, Which requires manual exploitation. This serivce allows the writing of a shell to the web root for the foothold. The www-data user is allowed to execute script as pepper user, and the script is vulnerable to command Injection. On further enumeration, systemctl is found to have SUID bit set, which is leveraged to gain a shell as root.